Update VMware Site Recovery Manager SSL Certs with your own Windows Domain CA Certificates using PowerShell
Next in the series of replacing vSphere related SSL scripts is the VMware Site Recovery manager script.
This script generates the SSL certificates based off of the WebServer Certificate Template and runs a batch file to perform the actual replacement.
#########################################################################################
Site Recovery Manager SSL Generation and Replacement script version 0.5
Tested on SRM 4.1 and 4.2
No guarantees, warranties, etc.
Blog post: https://goo.gl/g8x8U
#########################################################################################
Place the certs on a network location if your farm is larger than one server
$basedir = "\\fileserver\share\Certs"
Enter your vCenter server & username, you will be prompted for the password later.
$vcserver = "vcenter.base.local" $vcusername = "base\vmware"
Enter your Windows Certificate Authority information
below. Make sure it responds to certutil requests.
$rootCA = "dc.base.local" $rootCAName = "BASE-DC-CA" $email = "[email protected]" $org = "NetNerds" $city = "Kaplan" $state = "LA" $country = "US"
Enter the path of your openssl.exe (0.x and 1.x are supported).
If you don't have OpenSSL already, the script will download it for you.
$openssldir = "C:\OpenSSL-Win32"
##############################################################################################
You probably don't need to change anything below.
##############################################################################################
$srmregpath = "HKLM:\\SOFTWARE\\VMware, Inc.\\VMware vCenter Site Recovery Manager"
if (Test-Path $srmregpath) {
$srmreg = (Get-ItemProperty -Path $srmregpath)
$srmdir = $srmreg.InstallPath
} else { Write-Host "Site Recovery Manager not found. This script will now exist." ; exit }
$thisfqdn = ("$env:computername.$env:userdnsdomain").ToLower()
$srmserverip = \[System.Net.Dns\]::GetHostAddresses($vcserver)
$srmserverip = $srmserverip\[$srmserverip.GetUpperBound(0)\].IpAddressToString #ipv4
$openssl = $openssldir+"\\bin\\openssl.exe"
$wc = New-Object System.Net.WebClient
if (!(Test-Path "$basedir")) { $null = New-Item -Type Directory "$basedir" }
Write-Host -Foreground "DarkBlue" -Background "White" "Downloading root CA Cert.."
$url = "https://$rootCA/certsrv/certnew.cer?ReqID=CACert&Renewal=0&Enc=b64"
$root64 = "$basedir\\Root64.cer"
$wc.UseDefaultCredentials = $true; $wc.DownloadFile($url,$root64)
if (!(Test-Path($openssl))) {
Write-Host -Foreground "DarkBlue" -Background "White" "Downloading OpenSSL.."
$null = New-Item -Type Directory $openssldir
$sslurl = "https://openssl-for-windows.googlecode.com/files/openssl-0.9.8k\_WIN32.zip"
$sslzip = "$env:temp\\openssl.zip"
$wc.DownloadFile($sslurl,$sslzip)
$env:path = $env:path + ";$openssldir"
Write-Host -Foreground "DarkBlue" -Background "White" "Extracting OpenSSL.."
$shellApplication = new-object -com shell.application
$zipPackage = $shellApplication.NameSpace($sslzip)
$destinationFolder = $shellApplication.NameSpace($openssldir)
$destinationFolder.CopyHere($zipPackage.Items())
Remove-Item $sslzip
}
######################################################################
Generate Certs
######################################################################
Write-Host -Foreground "DarkBlue" -Background "White" "Generating service certs.."
$service = "$thisfqdn-srm"
$server = $thisfqdn.Substring(0,$thisfqdn.IndexOf("."))
$servicedir = "$basedir\\$service"
$servicecfg = "$servicedir\\$service.cfg"
$tempkey = "$servicedir\\temp.key"
$servicekey = "$servicedir\\$service.key"
$servicecsr = "$servicedir\\$service.csr"
$servicecrt = "$servicedir\\$service.crt"
$servicepfx = "$servicedir\\$service.p12"
$keyalias = "srm"
if (Test-Path($servicedir)) { $null = Remove-Item "$servicedir\\\*.\*" } else {$null = mkdir $servicedir }
Set-Content $servicecfg "\[ req \]"
Add-Content $servicecfg " default\_md = sha512"
Add-Content $servicecfg " default\_bits = 2048"
Add-Content $servicecfg " default\_keyfile = srm.key"
Add-Content $servicecfg " distinguished\_name = req\_distinguished\_name"
Add-Content $servicecfg " encrypt\_key = no"
Add-Content $servicecfg " prompt = no"
Add-Content $servicecfg " string\_mask = nombstr"
Add-Content $servicecfg " req\_extensions = v3\_req"
Add-Content $servicecfg "\`n\[ v3\_req \]"
Add-Content $servicecfg " basicConstraints = CA:FALSE"
Add-Content $servicecfg " keyUsage = digitalSignature, keyEncipherment, dataEncipherment"
Add-Content $servicecfg " extendedKeyUsage = serverAuth, clientAuth"
Add-Content $servicecfg " subjectAltName = DNS:$server, DNS:$thisfqdn, DNS:$srmserverip"
Add-Content $servicecfg "\`n\[ req\_distinguished\_name \]"
Add-Content $servicecfg " countryName = $country"
Add-Content $servicecfg " stateOrProvinceName = $state"
Add-Content $servicecfg " localityName = $city"
Add-Content $servicecfg " 0.organizationName = $org"
Add-Content $servicecfg " organizationalUnitName = $service"
Add-Content $servicecfg " commonName = $thisfqdn"
&$openssl req -new -nodes -out $servicecsr -keyout $tempkey -config $servicecfg
&$openssl rsa -in $tempkey -out $servicekey
Remove-Item $tempkey
certreq -submit -config ""$rootCA\\$rootCAName"" -attrib "CertificateTemplate:VMware-SSL" $servicecsr $servicecrt
&$openssl pkcs12 -export -in $servicecrt -inkey $servicekey -name $thisfqdn -passout pass:vmwaresrm -out $servicepfx
###############################################################################
Site Recovery Manager
###############################################################################
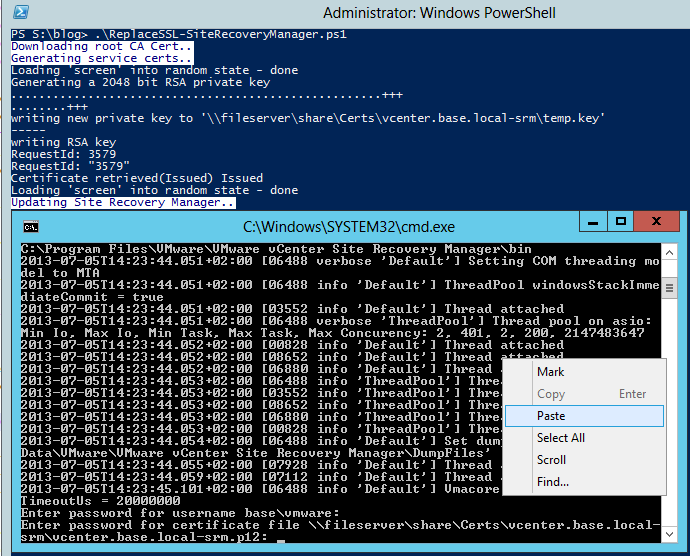
Write-Host -Foreground "DarkBlue" -Background "White" "Updating Site Recovery Manager.."
Stop-Service vmware-dr
$srmconfig = "$srmdir\\bin\\srm-config.exe"
$vcserverandport = "$vcserver" + ":80"
Set-Content "$basedir\\configure-srm.bat" "cd ""$srmdir\\bin\\"" & c: & srm-config.exe -cmd confcertbased -u $vcusername -crt ""$servicepfx"" -cfg ""$srmdir\\config\\vmware-dr.xml"" -extcfg ""$srmdir\\config\\extension.xml"" -vc $vcserverandport -sitename ""$vcserver"" & pause"
\[System.Reflection.Assembly\]::LoadWithPartialName("System.Windows.Forms") | Out-Null
\[System.Windows.Forms.Clipboard\]::SetText("vmwaresrm")
\[System.Windows.Forms.MessageBox\]::Show("Next, a box will appear and prompt you for your vCenter password and a certificate password.\`n\`nThe certifiate password 'vmwaresrm' has been copied to your clipboard.","Attention")
do {Start-Process -Wait "$basedir\\configure-srm.bat"
$sslsuccess = read-host "Was it successful? Y/N"
$i++
} until ($sslsuccess.ToUpper() -eq "Y" -or $i -gt 4)
if ($i -gt 4) { Write-Host "Too many failures. Script terminated."; Start-Service vmware-dr; exit}
Remove-Item -Force "$basedir\\configure-srm.bat"
Start-Service vmware-dr
###############################################################################
Finish
###############################################################################
Write-Host -Foreground "DarkBlue" -Background "White" "Done!"
Once you run the script, the batch file requires two inputs from you: the password for the specified vCenter Server admin variable and the PFX certificate password, "vmwaresrm"
To reduce the likelihood of errors, the script also places the certificate password into your clipboard, so you can just right-click, paste and hit enter.
Download ReplaceSSL-SiteRecoveryManager.ps1
All SSL Certificate Replacement Posts and Scripts in this Series