Update VMware View Composer SSL Certs with your own Windows Domain CA Certificates using PowerShell
Next in the series of replacing vSphere related SSL scripts is the VMware View Composer script. This one is rather simple, and uses certutil and certreq to generate the certificates, as opposed to OpenSSL.
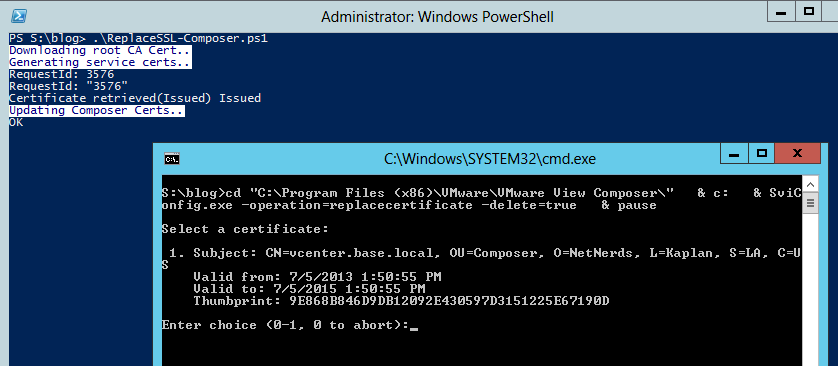
It also generates a batch script which calls SviConfig.exe. You just gotta put in a few variables, run the script and choose the new cert (I couldn't automate that part).
#########################################################################################
VMware Horizon View SSL Generation and Replacement script version 0.5
Tested on View 5.2
No guarantees, warranties, etc.
Blog post: https://goo.gl/bFApH
#########################################################################################
Place the certs on a network location if your farm is larger than one server
$basedir = "\\fileserver\share\Certs"
Enter your Windows Certificate Authority information
below. Make sure it responds to certutil requests.
$rootCA = "dc.base.local" $rootCAName = "BASE-DC-CA" $email = "[email protected]" $org = "NetNerds" $city = "Kaplan" $state = "LA" $country = "US"
View install directory
$viewdir = "C:\Program Files\VMware\VMware View"
##############################################################################################
You probably don't need to change anything below.
##############################################################################################
if ((Get-WmiObject Win32\_Service | where-object {$\_.DisplayName -like 'VMware View\*'}).Count -eq 0) {
Write-Host "No View Services found. Script terminating."; exit
}
$thisfqdn = ("$env:computername.$env:userdnsdomain").ToLower()
$backuptime = (Get-Date -uformat "%m%d%Y%H%M%S")
$backupdir = "$servicedir\\backup-$backuptime"
$certTemplate = "CertificateTemplate:WebServer"
if (!(Test-Path "$basedir")) { $null = New-Item -Type Directory "$basedir" }
Write-Host -Foreground "DarkBlue" -Background "White" "Downloading root CA Cert.."
$wc = New-Object System.Net.WebClient
$url = "https://$rootCA/certsrv/certnew.cer?ReqID=CACert&Renewal=0&Enc=b64"
$root64 = "$basedir\\Root64.cer"
$wc.UseDefaultCredentials = $true; $wc.DownloadFile($url,$root64)
######################################################################
Generate Certs
######################################################################
Write-Host -Foreground "DarkBlue" -Background "White" "Generating service certs.."
$service = "$thisfqdn-view"
$server = $thisfqdn.Substring(0,$thisfqdn.IndexOf("."))
$servicedir = "$basedir\\$service"
$servicecfg = "$servicedir\\request.inf"
$servicecsr = "$servicedir\\$service.csr"
$servicecrt = "$servicedir\\$service.crt"
$servicepfx = "$servicedir\\$service.pfx"
$keyalias = "vdm"
if (Test-Path($servicedir)) { $null = Remove-Item "$servicedir\\\*.\*" } else {$null = mkdir $servicedir }
Set-Content $servicecfg "\[Version\]"
Add-Content $servicecfg 'Signature="$Windows NT$"'
Add-Content $servicecfg "\[NewRequest\]"
Add-Content $servicecfg "Subject = ""CN=$thisfqdn, OU=View, O=$org, L=$city, S=$state, C=$country"""
Add-Content $servicecfg "KeySpec = 1"
Add-Content $servicecfg "KeyLength = 2048"
Add-Content $servicecfg "Exportable = TRUE"
Add-Content $servicecfg "MachineKeySet = TRUE"
Add-Content $servicecfg "FriendlyName=""vdm"""
Add-Content $servicecfg "SMIME = False"
Add-Content $servicecfg "PrivateKeyArchive = FALSE"
Add-Content $servicecfg "UserProtected = FALSE"
Add-Content $servicecfg "UseExistingKeySet = FALSE"
Add-Content $servicecfg "ProviderName = ""Microsoft RSA SChannel Cryptographic Provider"""
Add-Content $servicecfg "ProviderType = 12"
Add-Content $servicecfg "RequestType = PKCS10"
Add-Content $servicecfg "KeyUsage = 0xa0"
Add-Content $servicecfg "\[EnhancedKeyUsageExtension\]"
Add-Content $servicecfg "OID=1.3.6.1.5.5.7.3.1 ; this is for Server Authentication"
Add-Content $servicecfg "\[RequestAttributes\]"
Add-Content $servicecfg "SAN=""DNS=$thisfqdn&DNS=$server"""
$oldcert = (Get-ChildItem Cert:\\LocalMachine\\My -Recurse | Where-Object {$\_.Friendlyname -eq 'vdm'})
certreq -new $servicecfg $servicecsr
certreq -submit -config ""$rootCA\\$rootCAName"" -attrib $certTemplate $servicecsr $servicecrt $servicepfx
certreq -accept -machine $servicecrt
###############################################################################
Update View
###############################################################################
Write-Host -Foreground "DarkBlue" -Background "White" "Updating View Certs.."
$viewServices = (Get-WmiObject Win32\_Service | where-object {$\_.DisplayName -like 'VMware View\*' -and $\_.State -eq 'Running'})
Write-Host -Foreground "DarkBlue" -Background "White" "Stopping View Services.."
if ($viewServices -ne $null) {$viewServices | Stop-Service }
Write-Host -Foreground "DarkBlue" -Background "White" "Adding new certificate.."
$null = (New-Item -Type Directory $backupdir)
if ((Get-ChildItem cert:\\LocalMachine\\My -Recurse | Where-Object {$\_.Friendlyname -eq 'vdm'}).Count -gt 1) {
Write-Host -Foreground "DarkBlue" -Background "White" "Removing old certificate.."
$store = New-Object System.Security.Cryptography.X509Certificates.X509Store My, LocalMachine
$store.Open("ReadWrite")
$bytes = ($oldcert.export(\[System.Security.Cryptography.X509Certificates.X509ContentType\]::Cert))
$null = (\[System.IO.File\]::WriteAllBytes("$backupdir\\vdm.crt", $bytes))
$store.Remove($oldcert)
$store.Close()
}
if ($viewServices -ne $null) {$viewServices | Start-Service }
###############################################################################
Finish
###############################################################################
Write-Host -Foreground "DarkBlue" -Background "White" "Done!"
Download ReplaceSSL-Composer.ps1
Thanks to Tomas Fojta for the easy-to-understand tutorial.
All SSL Certificate Replacement Posts and Scripts in this Series