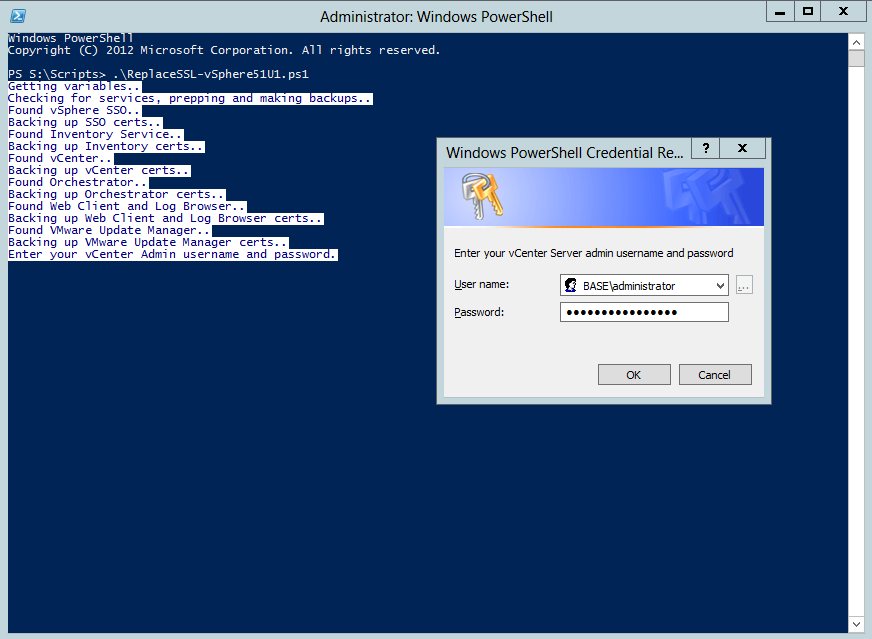
Update vSphere 5.1 SSL Certs with your own Windows Domain CA Certificates using PowerShell
One month ago when I finally got my vSphere lab set up, I had no idea that getting rid of those annoying untrusted SSL errors would be such a colossal undertaking. I have my own domain CA and thought it would be easy to automate the process of replacing the self-signed vSphere SSl certs with my own trusted certs.
At first, I attempted to use strictly Windows commands (certutil, certreq, etc) and PowerShell, but eventually gave in and incorporated OpenSSL into my script. Generating the certs were just the beginning, though.
Replacing the certificates in an automated fashion and getting each service to behave after the change was an extremely time-consuming task. VMware's documentation and KB articles leave a lot of room for improvement, but fortunately, Derek Seaman's blog was able to provide a lot of information that was either easy to miss, or missing entirely.
Numerous articles suggested using VMware's Certificate Automation Tool but the tool wasn't automated enough for my liking, even with supplemental scripts provided by other bloggers. I looked into guts of the Certificate Automation tool and, after a good bit of trial and error, replicated many of its techniques using PowerShell. Using these techniques, and following the suggestions found on forums and blogs, I was able to create a script that can replace the SSL certs of all of my vSphere lab servers in under 20 minutes, a majority of which is spent watching PowerShell stop and start services.
This script requires you to enter less than 15 variables as seen in the snippet below:
# SSO Server FQDN $ssoserver = "vcenter.base.local"
Place the certs on a network location if your farm is larger than one server
$basedir = "\\fileserver\share\Certs"
Enter your SSO master password below. You will be prompted for your vCenter Server
credentials at runtime.
$masteradmin = "admin@System-Domain" $masterpass = "Fakepass.123"
Enter your Windows Certificate Authority information below.
Make sure it responds to certutil and web requests.
$rootCA = "dc.base.local" $rootCAName = "BASE-DC-CA" $email = "[email protected]" $org = "NetNerds" $city = "Kaplan" $state = "LA" $country = "US"
Make sure you follow Derek Seaman's instructions
to create a new certificate template @ https://goo.gl/m98FE
$certTemplate = "CertificateTemplate:VMware-SSL"
Enter the path of your openssl.exe (0.x and 1.x are supported).
If you don't have OpenSSL already, the script will download it for you.
$openssldir = "C:\OpenSSL-Win32" $openssl = $openssldir+"\bin\openssl.exe"
You can see that the SSO admin username and password are in plain text. Unlike vCenter credentials, there was no easy way to validate the SSO username/password and the pros of placing the username and password there in plain text outweighed the cons. vCenter credentials were easier to validate and more of a priority for me to protect since they're usually Windows credentials.
Also, note that the default "Web Server" SSL certificate template is no longer sufficient. Please visit Derek Seaman's blog for instructions on how to create a certificate template which will work for all of the vSphere services.
"What it does.."
Start up
- If the server running the script is not the SSO server, it ensures the remote SSO Server's SSL certs have been updated first
- Checks the registry to see which vSphere services exist on the server running the script and sets service variables
- Creates the certificate directory if it does not exist
- Backs up all SSL Certs on the server
- Validates vCenter authentication if vCenter or VUM exist on the server
- Automatically downloads Root64.cer from the CA's web service
- Downloads and extracts OpenSSL if the files do not exist in the specified path
- Generates all SSL certificates for each of the services on the server. Uses server name + service name as the OU so that each cert can be distinguished.
If SSO service exists
- Stops SSO Service
- Generates new SSO keystore using the newly created SSO SSL certificate
- Copies Root64.cer to %programdata%\VMware\SSL\ca_certificates.cer
- Creates new hash file in %programdata%\VMware\SSL
- Updates SSO using rsautil.cmd
- Starts SSO Service
- Automatically builds service.properties and service_id files and stores them in %programdata%\VMware\ServiceIDs
- Reregisters all services using new root certificate
- Restarts SSO, and if they exist Log Browser, Web Client and Inventory services.
If Inventory service exists
- Unregisters Inventory service with SSO
- Stops Inventory service
- Copies new certs to the Inventory service SSL directory
- Starts Inventory Service
- Registers Inventory service with SSO
If vCenter service exists
- Copies new certs to the vCenter service SSL directory
- Using credentials previously entered, logs into vCenter service's mob website to automatically invoke reloadSslCertificate
- Restarts all vCenter related services
- Reregisters vCenter with Inventory Service
If WebClient services exists
- Stops WebClient and LogBrowser services
- Removes all files from SerenityDB directory
- Copies new certs to the Web Client and Log Browser service SSL directories
- Stops vCenter and Inventory Services if they exist on the local server
- Restarts SSO service on local or remote server
- Starts vCenter and Inventory Services if they exist on the local server
- Starts WebClient and LogBrowser services
If Update Manager exists
- Stops Update Manager services
- Copies new certs to the Update Manager service SSL directory
- Generates new Update Manager keystore using the newly minted Update Manager Certificates
- Updates registry entry with keystore password (testpassword)
- Runs vciInstallUtils to update VUM using credentials previously entered
- Starts Update Manager services
If Orchestrator exists
- Copies new certs to the Orchestrator service SSL directory
- Stops services if necessary
- Generates new Orchestrator keystore using newly created Orchestrator certificates
- Adds SSO Certificate to keystore
- Restarts Orchestrator services then returns them to their previous state of Running or Stopped
If you have vCenter servers in linked mode and are running the Web Client, you may run into the error message "Cannot connect to Inventory Service on [server]" when logging into the Web Client. I have not found a predictable way to fix this. Usually, it can be solved by first restarting the server running Web Client, then restarting the vCenter/Inventory server.
This script also has other limitations, many of them similar to the Certificate Automation Tool.
Limitations
Limitations specific to this script
- Only uses Windows Domain Certificate Authorities
- Does not account for intermediary CAs
- Has not been tested in large environments with HA and DRS
- Has not been tested with environments running: VMware Site Recovery Manager, vSphere Data Recovery, vCloud Director, or third-party solutions
- Does not have a rollback feature, yet. For rollback, I relied on Snapshots and database backups.
- Does not have advanced logging
- I don't recommend running this in a production environment until it's been vetted by far more people
Limitations that exist in VMware's tool that likely exist within this script
- vCenter Single Sign-On Password cannot contain spaces
- vCenter Orchestrator may fail to connect when using multiple vCenter Servers.
- You can update add additional vCenter Server SSL certificates using the VMO Configuration Webpage (https://vmoserver:8283/ default login: vmware/vmware -> vCenter Server -> SSL Certificates.
- Add all vCenter Certificates found in your Certs directory.
- Note that if vCenter and VMO are running on the same server, the vCenter cert will be automatically added.
- Client Not authenticated error when connecting to VMware Inventory service in Linked Mode Configurations. Wait 10 minutes and this should resolve itself.
Why I prefer using this script over VMware's
Requires minimal information and interaction
- Automatically downloads OpenSSL if neccessary
- Automatically generates the certificates based off of a few variables
- Automatically detects services and runs the SSL updates in the necessary order without user intervention
- If vCenter or VUM exists on the server, you wil be prompted for your vCenter credentials. This is the extent of interaction that the script will require:
Replaces all of the same certificates: SSO, Inventory Service, vCenter, Update Manager, Web Client/Log Browser, and Orchestrator
Also, works on vSphere farms with multiple servers (you must update the SSO server first)
It's all contained in just one (nearly 600 line) script
Works on 5.1 and 5.1U1
In the end, your Cert collection will look something like this:
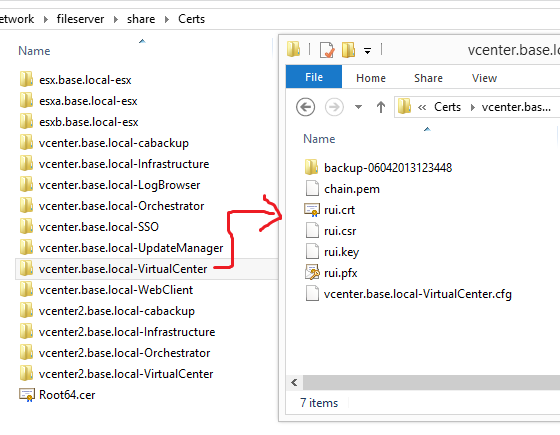
And each of your services will be encrypted with trusted certificates:
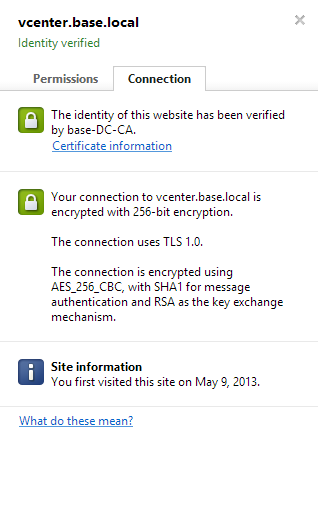
And, of course, Web Client, after a couple reboots. 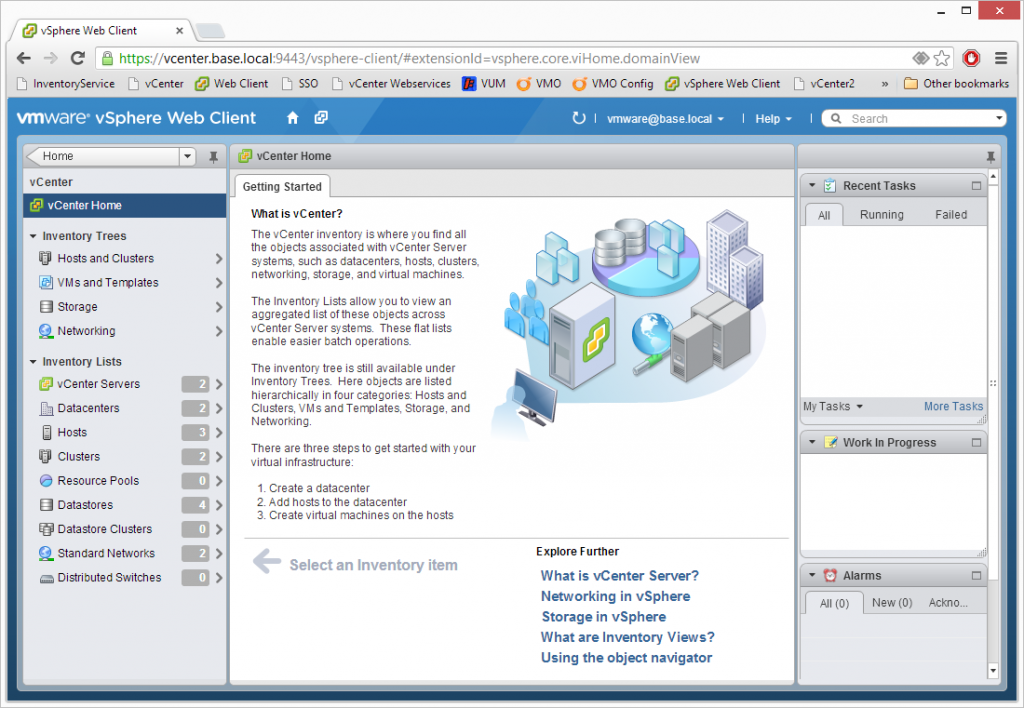
Getting started
- Ensure your Windows Domain CA certificate is trusted by members of your domain
- Take a snapshot of each vSphere server on which you will run this script
- Backup each of your databases
- Find a secure location on the network to store your certs (ie. \\fileserver\share\Certs)
- Visit Derek Seaman's blog and create a new certificate template
- Shut down the following services if they exist: VMware Site Recovery Manager, vSphere Data Recovery, vCloud Director, third-party solutions that connect to vCenter.
- Download the ReplaceSSL-vSphere51.ps1 script
- Change the variables
- Run the script first on the server running the SSO
- Run the script on all other servers
- If the Web Client connects to multiple vCenter servers, reboot the server running Web Client, as well as the server(s) running Inventory Service and vCenter.
- Consider running the complimentary ESX Script
Once the scripts are complete, you can visit each of your sites to confirm the SSL Certificates have been replaced. Please note that Log Browser and the Web Client take up to 5 minutes to fully restart.
Finally, bask in the glory of your trusted SSL certificates:
All SSL Certificate Replacement Posts and Scripts in this Series