Active Directory and PHP on Apache on Bash on Ubuntu on Windows
Recently, I wrote about Joining Ubuntu to an Active Directory Domain. That was for an actual Ubuntu box and the plan was that the next post would be about adding Apache to the mix. But then I got distracted by Apache on Bash on Ubuntu on Windows (check out my gists for sneak peaks).
I should be practicing for my upcoming sessions for PowerShell Conference EU 2016, but look at the reward!
First a few things that I remember that I've learned in this 2 day journey
- Apache is broken out of the box, but works if you mkdir /run/lock.
- The Linux are in C:\Users\username\AppData\Local\lxss\rootfs but don't try to edit them directly from Windows. They disappear from within bash or become corrupt.
- Instead, access /mnt/c and copy from within Linux.
- Samba doesn't work, but you don't need it for this. SSSD doesn't either.
- You can access bash's Apache from Windows no sweat, but Kerberos within Linux doesn't like localhost or the hostname when going between hosts. Make an extra A record to deal with that.
Getting Started
First, part of this is done in Windows because ktpass is required. The Ktpass command-line tool "allows non-Windows services that support Kerberos authentication to use the interoperability features provided by the Kerberos Key Distribution Center (KDC) service."
Basically, it creates a binary file that contains some encrypted stuff that authenticates as a valid AD user.
ktadd is Linux's equivalent of ktpass. If you see it mentioned while you're setting up interoperability, it's not applicable to Active Directory. ktpass.exe is supposedly found Remote Server Administration Tools for Windows or RSAT, but that wasn't my experience with Windows 10. It's nowhere to be found on my 64-bit machine. Instead, I Enter-PSSession to my domain controller because all of my testing is done in a lab environment so it's acceptable.
Now for my setup
- Active Directory domain: example.local
- Service acct: EXAMPLE\ubuntuauth
- Service acct pass:
- Win 10 w/bash workstation name: wslhost.example.local
- Secondary DNS name: localweb.example.local
- Firewall allows port 80
"Wait, why is a secondary hostname needed? I just wanna hit https://localhost." Because I think Bash on Windows confuses Kerberos. Or maybe that's just the way it's supposed to work, if anyone knows, feel free to comment.
In this example, open http://localweb in your browser. Since the localweb hostname set in my DNS, it worked both locally and remotely for me.
The Windows Part
1\# Run this on a Domain Controller or a workstation with ktpass
2$keytab = 'C:\\temp\\httpd.keytab'
3
4ktpass /princ HTTP/nimy.example.local@EXAMPLE.LOCAL /mapuser EXAMPLE\\ubuntuauth /crypto ALL /ptype KRB5\_NT\_PRINCIPAL /mapop set /pass <SecurePasswordHere> /out $keytab
5ktpass /princ HTTP/localweb.example.local@EXAMPLE.LOCAL /mapuser EXAMPLE\\ubuntuauth /crypto ALL /ptype KRB5\_NT\_PRINCIPAL /mapop set /pass <SecurePasswordHere> /in $keytab /out $keytab
6
7# Copy keytab to Windows 10 if you ran it on the DC. THIS IS SUPER COOL.
8$session = New-PSSession -ComputerName dc
9Copy-Item -Path $keytab -Destination C:\\temp -FromSession $session
The Bash on Ubuntu on Windows Part
1Initially, you'll install a few packages and krb5-user will actually prompt you for a few things then write it all out to /etc/krb5.conf
2
3\# Install required packages kerb
4# First prompt: EXAMPLE.LOCAL (in caps)
5# Second and third prompt: lowercase FQDN of your domain controller(s)
6apt-get -y install krb5-user apache2 libapache2-mod-auth-kerb
7
8Capitalization is important for the default realm.
9
10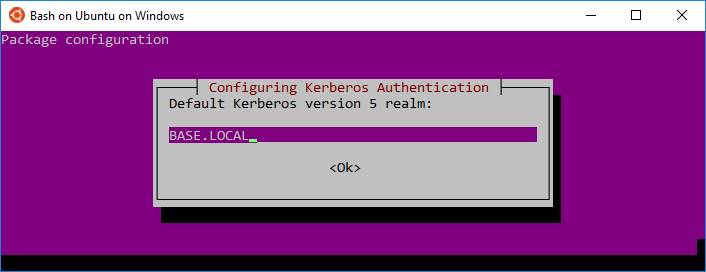
11
12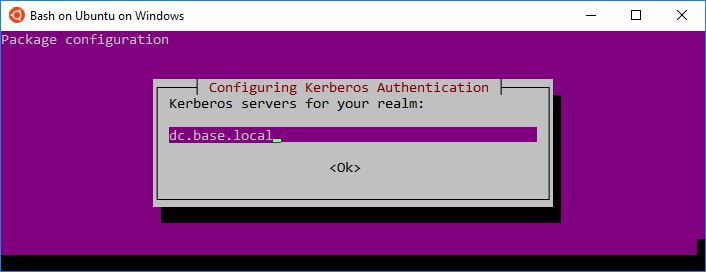
13
14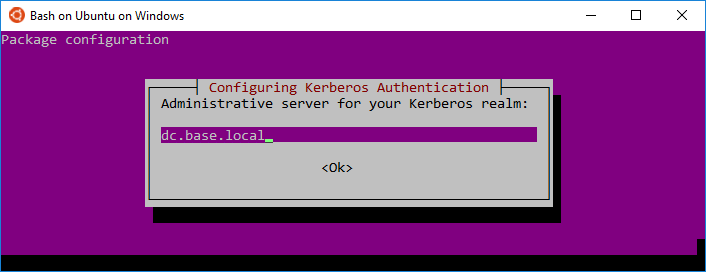
15
16If you don't see this all in a row, don't panic. It flips back to the default black screen while it sets up the configuration files. That's actually it for the Kerberos part, mostly. Now it's time to test and then setup Apache.
17
18\# Get a ticket to confirm your krb is working
19kinit ubuntuauth
20
21# Look at your ticket list
22klist
23
24# Move keytab to etc and change permz
25cp /mnt/c/temp/httpd.keytab /etc/
26chmod ugo+r /etc/httpd.keytab # demo convenience; prefer restrictive perms like chown root:www-data && chmod 640
27
28# Check key entries
29klist -k /etc/httpd.keytab
30
31# Make Apache work
32
33# mktemp: failed to create directory via template '/var/lock/apache2.xx': No such file or directory
34# This is because /var/lock is a symbolic link to something that doesn't exist (/run/lock)
35mkdir /run/lock
36
37# make annoying warnings go away
38echo "Listen 0.0.0.0:80" > /etc/apache2/ports.conf
39echo "ServerName localhost" > /etc/apache2/conf-available/fqdn.conf
40a2enconf fqdn
41
42# add kerb authentication to Apache and enable it
43echo "
44 <Location />
45 AuthType Kerberos
46 KrbMethodNegotiate on
47 KrbMethodK5Passwd off
48 Krb5Keytab /etc/httpd.keytab
49 Require valid-user
50 </Location>
51"> /etc/apache2/conf-available/kerbauth.conf
52a2enconf kerbauth
53
54# Now start Apache!
55service apache2 start
56
57# Look at the logs if you'd like to see yourself authenticating
58tail /var/log/apache2/access.log
59
60That's it, now you can hit the service using a web browser :D Open up **http://localweb** in Chrome and check it.
Want the PHP part?
1apt-get -y install php5 libapache2-mod-php5
2
3echo '<?php
4 echo "<center>
5 <strong><br>Welcome Active Directory user {$\_SERVER\['PHP\_AUTH\_USER'\]}
6 <br>to PHP on Apache on Bash on Ubuntu on Windows
7 <br><br><img src=/icons/ubuntu-logo.png>
8 </center>";
9?>
10' > /var/www/html/test.php
11service apache2 force-reload
Then go to http://localweb/test.php in your browser
Ain't she a beaut?
Wanna see this all in one shot? Here's the Gist. If you're into integrated authentication, there are other gists there that you may enjoy.